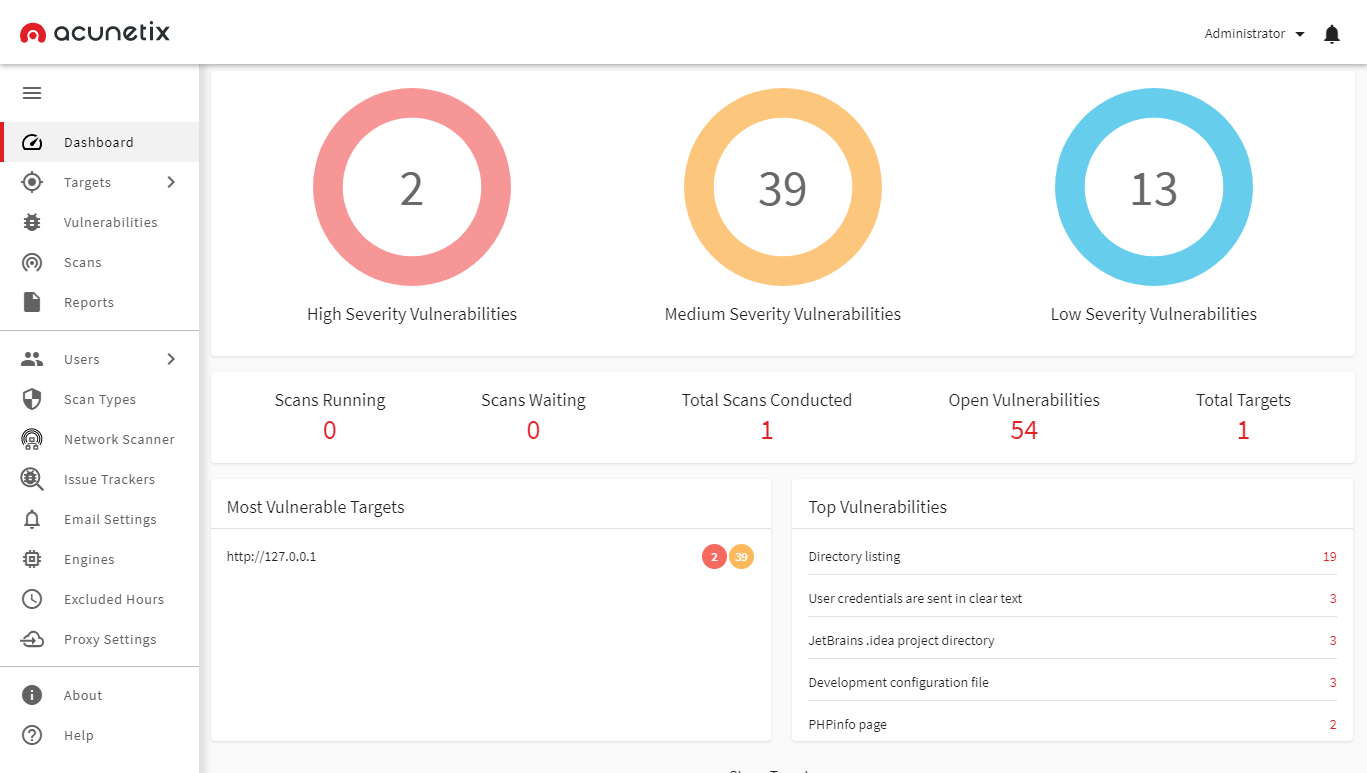
0x01 工具简介
AWVS是一款自动化应用程序安全测试工具,支持windows平台,主要用于扫描web应用程序上的安全问题,如SQL注入,XSS,目录遍历,命令注入等。
- 下载地址:https://pan.baidu.com/s/1C7hykrhI7UPoe75vUyp5YQ
- 提取码:
clfs
0x02 安装破解
先按照正常流程安装好AWVS13工具
工具安装完成后进行破解
# 破解过程{正确打开方式–安装–复制–替换}
1. 将wvsc.exe覆盖到“C:\Program Files (x86)\Acunetix\13.0.200205121\”
2. 将license_info.json覆盖到“C:\ProgramData\Acunetix\shared\license”破解完后即可使用
0x03 批量扫描
由于AWVS应用本身没有批量扫描的功能,所以只能够通过脚本调用AWVS的API接口进行批量添加扫描网址。
这个AWVS批量扫描脚本是之前在玄魂工作室发布的一篇文章里看到的,亲测可用。
使用这个脚本要注意的地方:
1、找到脚本中的 self.api(大概33行左右)替换成你自己AWVS里的APIkey
2、找到脚本中的self.speed(大概39行左右)设置扫描的速度(sequential|slow|moderate|fast),默认为fast
3、在脚本同目录下新建一个awvs.txt的文件,在里面导入你要批量扫描的网址,格式如下:
http://www.test1.com/
https://www.test2.com/
http://api.test3.com/
......4、脚本运行后会出现三个选项,第一个选项是导入awvs.txt的网址启动扫描;第二个选项是删除之前所有的扫描记录,慎用!
import json
import queue
import requests
requests.packages.urllib3.disable_warnings()
def run():
print(' ______ ____ __ __ ')
print('/\ _ \ /\ _`\ /\ \__ /\ \ ')
print('\ \ \L\ \ __ __ __ __ __ ____ \ \ \L\ \ __ \ \ ,_\ ___\ \ \___ ')
print(" \ \ __ \/\ \/\ \/\ \/\ \/\ \ /',__\ \ \ _ <' /'__`\ \ \ \/ /'___\ \ _ `\ ")
print(" \ \ \/\ \ \ \_/ \_/ \ \ \_/ |/\__, `\ \ \ \L\ \/\ \L\.\_\ \ \_/\ \__/\ \ \ \ \ ")
print(" \ \_\ \_\ \___x___/'\ \___/ \/\____/ \ \____/\ \__/.\_\\ \__\ \____\\ \_\ \_\ ")
print(' \/_/\/_/\/__//__/ \/__/ \/___/ \/___/ \/__/\/_/ \/__/\/____/ \/_/\/_/')
print(' ______ __ ')
print(' /\__ _\ /\ \__ ')
print(' \/_/\ \/ ___ ___ _____ ___ _ __\ \ ,_\ ')
print(" \ \ \ /' __` __`\/\ '__`\ / __`\/\`'__\ \ \/ ")
print(' \_\ \__/\ \/\ \/\ \ \ \L\ \/\ \L\ \ \ \/ \ \ \_ ')
print(' /\_____\ \_\ \_\ \_\ \ ,__/\ \____/\ \_\ \ \__\ ')
print(' \/_____/\/_/\/_/\/_/\ \ \/ \/___/ \/_/ \/__/')
print(' \ \_\ ')
print(' \/_/ ')
print("\n")
print(' Github:https://github.com/BetterDefender/AwvsBatchImport.git')
print(' Author:BetterDefender')
print(' Version:1.1')
class AwvsScan(object):
def __init__(self):
self.scanner = 'https://127.0.0.1:3443' # Modify URL
self.api = '1986ad8c0a5b3df4d7028d5f3c06e936c9c77171759f347dd8426737ab9736f9d' # Modify API
self.ScanMode = '11111111-1111-1111-1111-111111111111' # ScanMode
self.headers = {'X-Auth': self.api, 'content-type': 'application/json'}
self.targets_id = queue.Queue()
self.scan_id = queue.Queue()
self.site = queue.Queue()
self.speed = 'fast' #修改扫描速度为sequential|slow|moderate|fast即可,默认为fast
def main(self):
print("")
print("|"+'=' * 35+"|")
print("|Please select the function to use:|")
print("""| 1.Add scan task using awvs.txt |\n| 2.Delete all tasks |\n| 3.Regulae all tasks's speed |""")
print("|"+'=' * 35+"|")
choice = input(">")
if choice == '1':
self.scans()
if choice == '2':
self.del_targets()
if choice == '3':
self.speed_regulate()
self.main()
def openfile(self):
with open('awvs.txt') as cent:
for web_site in cent:
web_site = web_site.strip('\n\r')
self.site.put(web_site)
def targets(self):
self.openfile()
while not self.site.empty():
website = self.site.get()
try:
data = {'address': website,
'description': 'awvs-auto',
'criticality': '10'}
response = requests.post(self.scanner + '/api/v1/targets', data=json.dumps(data), headers=self.headers,
verify=False)
cent = json.loads(response.content)
target_id = cent['target_id'] #获取任务target_id
self.targets_id.put(target_id)
except Exception as e:
print('Error:Target is not website! {}'.format(website))
print("Please check if the URL in awvs.txt is correct!")
exit()
def scans(self):
self.targets()
while not self.targets_id.empty():
data = {'target_id': self.targets_id.get(),
'profile_id': self.ScanMode,
'schedule': {'disable': False, 'start_date': None, 'time_sensitive': False}}
response = requests.post(self.scanner + '/api/v1/scans', data=json.dumps(data), headers=self.headers,
allow_redirects=False, verify=False)
if response.status_code == 201:
cent = response.headers['Location'].replace('/api/v1/scans/', '')
#print(cent)
def get_targets_id(self):
response = requests.get(self.scanner + "/api/v1/targets", headers=self.headers, verify=False)
content = json.loads(response.content)
for cent in content['targets']:
self.targets_id.put([cent['address'], cent['target_id']])
def del_targets(self):
while True:
self.get_targets_id()
if self.targets_id.qsize() == 0:
break
else:
while not self.targets_id.empty():
targets_info = self.targets_id.get()
response = requests.delete(self.scanner + "/api/v1/targets/" + targets_info[1],
headers=self.headers, verify=False)
if response.status_code == 204:
print('delete targets {}'.format(targets_info[0]))
def speed_regulate(self):
while True:
self.get_targets_id()
if self.targets_id.qsize() == 0:
break
else:
if not self.targets_id.empty():
for i in range(self.targets_id.qsize()):
targets_info = self.targets_id.get()
data = {'scan_speed':self.speed}
response = requests.patch(self.scanner + "/api/v1/targets/"+targets_info[1]+'/configuration', data=json.dumps(data), headers=self.headers,verify=False)
if response.status_code == 204:
print('Regulate targets {}'.format(targets_info[0]))
break
if __name__ == '__main__':
run()
Scan = AwvsScan()
Scan.main()
